Vol. 9 No. 1, October 2003
| Vol. 9 No. 1, October 2003 | ||||
Gary Burnett | Michael H. Dickey | |
School of Information Studies | College of Business |
People engaging in electronic exchanges can create communities—places with socially constituted norms, values, and expectations. We adopt an anthropological perspective, yoked with a methodology based in hermeneutics, to illustrate how language use both reflects and influences culture in a virtual community. Our study analyses contributions to a Usenet newsgroup. Four elements of our conceptual model—coherence, reference, invention, and intention—provide mechanisms to examine a community's texts as it engages in social interaction and knowledge creation. While information exchange and socializing are intertwined, our model allows a robust understanding of the relationship between the two. Texts are not merely vehicles for communication but serve multiple purposes simultaneously. While they transfer information, texts also provide information within a social context, and create an expanding archive of socially-contextualized information well beyond the capabilities of any individual participant. This allows groups to negotiate reputations, socialize, and define the limits of their knowledge.
People in virtual communities use words on screens to exchange pleasantries and argue, engage in intellectual discourse, conduct commerce, exchange knowledge, share emotional support, make plans, brainstorm, gossip, feud, fall in love, find friends and lose them, play games, flirt, create a little high art and a lot of idle talk. (Rheingold, 1993, p. 3)
It is now generally accepted that people engaging in electronic exchanges are able to create communities—places with socially constituted norms, values, and expectations. Text serves as the lifeblood of these electronic places, conveying the ideas and feelings of participants that lead to the growth and evolution of a community or to its demise. We propose an approach grounded in linguistic anthropology and hermeneutics to shed light on culture, as it is enacted in virtual communities. As we examine a given community, we gain understanding into how culture is created and evolves.
In the course of interaction, virtual communities are confronted with a series of challenges brought about not only by the subjects they discuss, but also by limitations and complexities of the technology through which they must interact, as well as by the texts that they write, read, and interpret. This project examines a specific community, looking at it through its texts, with an eye toward understanding how the hermeneutic activities reflected in these texts—the community's own attempt to understand the process through which they interact lead to the success or failure of virtual communities. We adopt an anthropological perspective, yoked with a methodology based in hermeneutics, to illustrate how language use both reflects and influences culture in a virtual community. We begin by describing how text reflects culture and then present a conceptual model based on this perspective. Next, we describe a study and the methods used to analyse selected postings to a Usenet newsgroup. Then we present our analysis. We conclude with a discussion of our findings and methodological approach, and implications for future research.
In this section, we begin with a brief overview of the major issues associated with virtual communities, followed by a description of our approach for studying them.
Virtual community has come to mean many different things, but often refers to interconnected groups of individuals who use one of a number of computer-mediated communication forums—including Usenet newsgroups, listservs, Web-based discussion groups, etc.—to share interests, activities, and goals. When Rheingold brought the WELL to the reading public in 1993, the idea of having a 'daily life in cyberspace' (p. 38) was new to many in the audience. The WELL represented one kind of virtual community, built in a text-based environment, and, at least at first, primarily based in one geographic area (Rheingold, 1993). Over the decade since publication of The virtual community, various types of virtual communities have been studied, and various definitions of the term have been—and continue to be—proposed and debated, including:
The concept of virtual community is consistent with the concept of a community of practice, in which members actively participate in community practices and construct identities in relation to the community (Wenger, 1998). A virtual community is comprised of members 'bound together for mutual service' (Schultze & Orlikowski, 2001: 55). Members of virtual communities tend to provide advice and solutions to problems expressed by other members, even though they may be strangers to one another (Constant et al., 1996). In virtual communities of practice, information is shared not on a quid pro quo basis, but on the basis of generalized reciprocity (Wasko and Faraj, 2000).
There have been other foci in looking at multi-person interactions on a large scale using computer mediated communication. DeSanctis and Monge (1998) indicate that virtual organizations need research support the better to manage communications for individuals and groups. Monge and Contractor (2000) encourage focus on the communication networks that emerge among individuals, groups, and organizations. Teams and groups can also interact online, creating focused, multi-party virtual collectives on a smaller scale (McGrath & Hollingshead, 1994; Turoff, et al., 1999). Focusing instead on the technology used for virtual community, writers such as Preece (2000) and Kim (2000) have focused on the design of computer systems built to encourage members to participate. On the other end of the spectrum, some research has explored the communicative role of individuals and the text they produce as the basis of their participation (Herring, 1999; Walther, 1996). Quantitative survey and social network analysis have been joined by virtual ethnography (Hine, 2000) and cyber-archaeology (Jones, 1997) as further methods of studying community online.
Textual communication is pivotal to understanding virtual communities, for it is how participants in those virtual environments create, affirm, or change shared meaning and culture. Hermeneutics, the 'study of interpretation, especially the process of coming to understand text' (Boland, 1991: 439) provides an ideal framework for analysing and understanding the activities and significance of online places inhabited by communities of writers and readers of the shared texts that form the basis of their interaction. The mechanisms of interpretation are the means through which online places are able to create robust cultural environments.
One of the cornerstones of Paul Ricoeur's hermeneutic theory is the 'mode of "as if" ("as if you were there"),' (1976: 35) a process through which the texts of certain genres restructure the contextual cues that form a fundamental part of spoken discourse. By extension, this 'mode of "as if"' creates a kind of virtual 'place' through the mediation of the text. Because they exist through the creation and reception of texts, virtual communities depend directly upon this 'mode of "as if"'. These communities are inhabited by participants who converse textually with each other 'as if' they were actually present within a specific place (Burnett, 2002). Understanding text requires uncovering values and norms embedded in the surrounding community's language. The objective of hermeneutics is to understand how participants understand their environment or in other words, the development of an 'understanding of understanding' (Geertz, 1983: 5).
Studies of communities of practice have suggested that 'narration,' 'collaboration,' and 'social construction' function together in important ways to disseminate knowledge and build group cohesion outside the formal structures of an organization (Orr, 1990). Thus, the collective knowledge of a group—the particular body of information that gives it definition—cannot be separated from the social context in which it occurs (Brown and Duguid, 1991).
Since understanding is necessarily context dependent, we can glean guidance from philology. Philology, or the 'text-centered study of language' (Becker, 1979: 212), focuses on explaining the relationship between texts and the context in which they are written. Rather than simply providing verbatim translations of texts, careful philologists also provide detailed annotations that help the reader interpret the text (Geertz, 1983). This approach assumes that individuals bring cultural biases to their readings of text, which in turn, affect interpretations. Detailed descriptions of context are necessary so that readers may ascribe meaning more accurately (Becker, 1979; Geertz, 1983). This philological perspective for hermeneutic analysis has been dubbed cultural hermeneutics (Geertz, 1983).
The conceptual model, developed by Dickey, et al. (2002), and shown in Figure 1, represents a virtual community. The innermost ellipse represents the process of communicating with text. At its core is inscription of action, which refers to the recording of activity by virtual community members. Inscription results in the creation of text, which can then be interpreted by one or more other participants in the environment. The interpretation(s) in turn may or may not result in additional inscriptions.
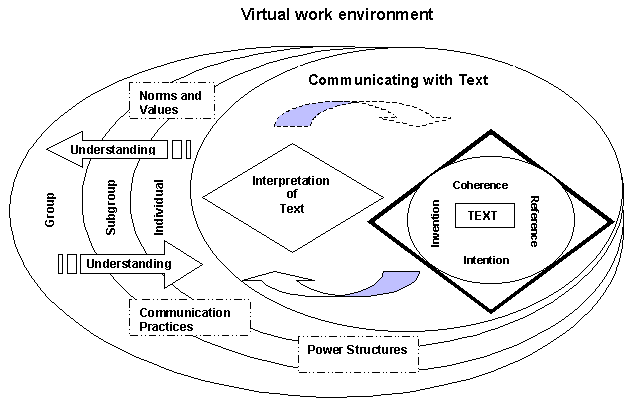
The interpretation of text is dependent upon the context in which it is written. In other words, accurately to interpret or ascribe meaning, we must situate the text within a multi-faceted context (Geertz, 1983). We understand this context by investigating the relations of the text to various contextual facets (Becker, 1979). Four important contextual relations are: coherence (the relation of textual units to other textual units in the text); invention (the relation of text to associated texts); intention (the relation of text to its creator or creators); and reference (the relation of text to non-literary events) (Becker, 1979; Geertz, 1983). In addition to the interpreted meaning(s) of text, the shared understanding of social structures influences inscriptions. Social structures and processes particularly relevant to virtual communities include communication practices, power structures, and norms and values. While social structures shape inscriptions, the content and interpretation of them may also lead to changes in them over time (Giddens, 1984).
The outer ellipses in the model depict differences in understanding of a virtual community's culture. Individual understandings may be unique, or may be congruent with the understandings of other individuals, subgroups of individuals, or everyone participating in the virtual community.
This paper reports on a study that applies these concepts to practice by analysing contributions to a Usenet newsgroup devoted to firewall technology. We begin by describing the methods used for the study, then turn to analyses of four different samples drawn from this community over the course of six weeks during the summer of 2002, after which we provide some conclusions and directions for future research. Our goal is to provide a rich understanding of the ways in which text creates and sustains culture in such environments.
We should note, in passing, that we do not address here the question of whether the norms and values articulated through the texts exchanged by participants in the virtual community are salient for (or representative of) those participants in their day-to-day lives outside of their textual interactions within the community. That is, we are observing the participants through what they write within the context of a specific online environment, not drawing conclusions about the relationship between that environment and their lives outside it. Our argument is not that there is no relationship between activities within the virtual community and the lives of participants in other contexts, but, rather, that the enactment and expression of norms, values, and interests in the texts exchanged by community members can tell us a great deal about the norms and interests within the framework of the textually-mediated community itself.
We conducted this study to apply our ideas to practice by analysing contributions to a Usenet newsgroup, comp.security.firewalls. Although it currently uses the infrastructure of the Internet as its primary mechanism for distributing messages, Usenet preceded the Internet as a large-scale, many-to-many communications medium, and it has, over time, developed its own norms and standards for interactions. Newsgroup messages are distributed from server to server, where they are stored and made available to participants who must use special 'newsreader' software to download, read, and create messages. Thus, unlike listservs, which come directly to participants, newsgroups must be actively sought out; while listservs are 'pushed' to participants, newsgroups must be 'pulled' from the server. Further, because server administrators maintain local control, determining not only which newsgroups to offer, but also establishing policies for how long messages are stored before they are deleted, the set of messages available at any given time may be radically different from server to server.
The requirement that participants use special software to participate in newsgroups further influences the perceived social terrain of Usenet, because different newsreaders provide radically different capabilities for organizing and accessing messages.2 Some newsreaders, like tin, tass, and nn, are themselves server-based, and require users to type commands to read and write messages. Others, including popular Web browsers like Netscape and Microsoft's Internet Explorer, are 'client' readers, which reside on the participants' own computers and often function much like other browser components. Participants can also, depending on their software, customize their own view of newsgroups, sometimes making significant changes in which posts from a newsgroup they see. For instance, a participant who does not wish to read the posts of another participant can create a 'killfile' which prevents all of that participant's posts from being displayed by the newsreader without impacting the blocked participant's ability to post or the ability of others to read the blocked posts. Users can also pick and choose which messages they read, opting to limit their view of a newsgroup to either posts written by a select group of participants or posts on a select set of topics.
Thus, individual participants may have very different views of the current status of any newsgroup at any given time simply because of differences in server policy and newsreader characteristics. Given such variability in what individuals see of a newsgroup, it is impossible to claim that there are clear boundaries to any given newsgroup or that there is a single 'correct' version of a newsgroup. Rather, the content of a newsgroup is, in part, determined for any given participant at any given time by the set of constraints imposed by the server and newsreader software and the choices of the participant.
The current study uses a series of different 'slices' of newsgroup activity to reflect the variability of possible views of a Usenet newsgroup. All messages from the newsgroup appearing on the news server at a major university in the south-eastern United States during a six-week period in the summer of 2002 were downloaded and archived. From this full archive of nearly 2000 posts by several hundred participants, the following samples were extracted and used for analysis:
Each of these groupings of posts was printed and examined using the framework described in the conceptual model. The objective of this study is to test the basic concepts of the model and to examine the extent to which this analysis sheds light on culture in virtual communities. While each of these samples is limited and, in some regards, problematic (such deficiencies will be discussed below), the use of multiple samples of the data for analysis, because it reflects differences in the ways in which community participants view the newsgroup, allows a better understanding of the context of exchanges, and a richer description of the norms and communication practices that characterized the newsgroup. Each sample was analysed by at least two of the four authors and coded to reflect the four contextual relations (coherence, reference, invention, and intention) described in Figure 1. These concepts were operationalized as follows:
For each of the four samples of textual communication, we begin with an overview of the sample, followed by our analysis in terms of coherence, reference, invention, and intention. We conclude with an overall characterization of the community's culture, as represented by that sample, along with limitations of the sample.
This sample provides, perhaps, the most 'natural' view of the newsgroup, since it simply extracts every message present on the news server during a specific period of time, without giving preference to individual posters or threads. Since most newsreaders offer the capability of sorting messages by a variety of criteria, including sender and subject, the sample is not the only possible view of the community. It does, however, provide a good illustration of the range of posts and participants to be found there. During the 20 hours represented by this sample, 40 separate individuals posted messages on 32 different topics (including one example of sexually-oriented spam). Only two posters in this sample were among the five most prolific posters to the group. The activity represented by this sample can be considered to be very nearly independent of that found in our other samples, although it is linked to the others by the overall subject concerns of the newsgroup and by the social and textual norms it contains.
Coherence describes the set of socially established textual constraints and norms to be found within a specific group, and specifies the standard 'look and feel' of the texts exchanged by that group. In a Usenet newsgroup, elements of coherence will include the presence or absence of signature files (or 'sigs'), the level of technical or other jargon in the posts, the choice of an individual poster to use their real name and e-mail address or not, as well as norms of grammar and usage.
Given Usenet's long history, many of these elements of coherence are generic to Usenet as a whole, while others are specific to given groups. Many newsgroups make such norms explicit through the creation of Frequently Asked Questions files (FAQs), which are posted on a regular basis to the group and made available on the World Wide Web (Burnett & Bonnici, 2003). However, the newsgroup under observation, like others devoted to computer security, does not maintain a FAQ to articulate social or textual norms, preferring to use the FAQ to address technical aspects of firewalls only. Thus, an unstated norm of coherence in this newsgroup is that posts are expected to limit themselves to such technical issues, omitting any other information. Perhaps as a result, while certain elements of coherence were consistent throughout the fifty posts, others were quite variable.
In general, posts in this sample reflected this norm, containing some degree of technical jargon, and there is an overall sense that all readers of the group would understand such jargon, since they all share a common interest in the technical aspects of firewalls. One short thread within the sample made joking reference to the necessity for such jargon in a technical setting, with one poster mentioning the 'arcane settings' required by a particular piece of firewall software and another responding that whether or not the settings were 'arcane' depended upon the knowledge of the user. Indeed, many of the posts in the sample were free enough in their use of technical jargon that non-technically oriented readers would find the posts quite difficult to follow.
Over time, Usenet has become notorious as a source for e-mail addresses used by spammers to send out unsolicited messages to large numbers of people. Given that the newsgroup is focused on issues related to computer security and firewalls, it might be expected that participants would demonstrate a strong tendency to protect themselves from receiving spam by altering or falsifying the e-mail addresses they attach to their messages; it might also be expected that participants would use pseudonyms rather than real names. However, only ten posters in this sample used false or modified e-mail addresses; similarly, only fourteen used pseudonyms to mask their identities. Of the 22 posters who used signature files to identify themselves, only two used files that overtly addressed security concerns by including anti-spam and encryption information.
Norms of grammar, usage, and message structure tended towards informality, often relying on truncated sentence fragments, although several posters mimicked the formal structure of letters in their posts, including full salutations and closings. The tone of posts, overall, was conversational, even in the most highly technical messages. For example, in response to a request to post firewall logs to the group, one person responds:
I'd rather not. I rack up a 1MB file log file each day just off my Linksys alone, and my home server logs contains a little too much personal site info to post here.
Reference, through which external non-textual events or objects enter the texts of a group, is the primary way in which groups define and control their terrain of subjects and interests. A group remains 'on-task' to the extent their posts reflect a shared set of external references rather than indulging in 'topic drift'. The newsgroup, with its sharp focus on the nuts and bolts of computer firewalls, relied consistently on the materials and procedures of firewall technologies, referring to such things as the installation and maintenance of hardware, the benefits and drawbacks of specific software packages, and the use and interpretation of log files. The only post of the fifty that utilized references not related to firewalls was the single instance of spam in the sample. Thus, this sample suggests that the group preserves a strong, shared universe of references and has little time or interest, at least in the newsgroup itself, for other issues.3
Individual threads provide perhaps the best mechanism for analysing invention, because of the ways in which they often begin through the posting of a query or the description of a problem, and conclude with an example of 'speaking the present' through the posting of an answer or a solution. Because this sample of fifty consecutive posts includes only partial threads, instances of invention were less clearly defined here than in our other samples. However, twenty-two of the fifty posts made explicit reference to external documentation and other information sources, thus answering questions by 'speaking the past' contained in existing texts.
Posts in this sample also provided several interesting examples of the relationship between information emerging from the expertise of the participants and information already documented in existing sources. Several posts made explicit reference to the need of the group to invent new knowledge because of the lack of or the poor quality of existing documentation; for example, one poster noted that 'Microsoft has really no documentation or TID's on which ports OWA 2000 needs to use ....' Most interestingly, two posters explicitly commented on the value of creating new information via the texts created by newsgroup participants, including one who closed a post by writing:
please keep me informed of your findings. (please, send me a copy by e-mail as well !)
In a situation in which existing information resources—those that 'speak the past'—are lacking, the invention of new knowledge is of particular importance, and newsgroup participants appear to be acutely aware of the value of that aspect of their interaction.
Perhaps because of their consistently strong focus on the subject area of the newsgroup, participants in essence accepted a single over-arching intention for all of their posts in this sample: to share information related to the implementation, management, and configuration of firewall technologies.
Within this framework, individual posts, of course, reflected other more specific intentions. These include searching for information, attempting to solve a problem, providing bibliographic references, providing trouble-shooting assistance, and criticizing existing documentation or firewall technologies. Most posts did not make these intentions overt, since they are all part of the governing intention of the group. A handful of posters, however, made direct reference to their intentions through phrases such as 'I am now seeking information here,' or 'I hope this helps anybody who finds themselves trying to trouble shoot ....' Such a paucity of direct markers of intention may be the result of the strength of the shared intention of the group as a whole. That is, when all participants are in agreement about their goals, they do not feel the need to state them directly, but can simply assume that their intentions will be accepted and understood by others within the group.
As viewed through the lens of a randomly selected sample of fifty consecutive posts, the community found in the newsgroup appears to be quite atypical of those found in Usenet generally. In the place of seemingly endless flame wars and large numbers of spamming messages, this sample reveals a community keenly focused on its area of interest. In addition, while some posters are slightly more active than others within the sample, the work of the group—on-going troubleshooting and sharing of information—is evenly spread among a number of people who share a set of concerns while treating each other with respect and consideration. In this sample, very little time is spent off-task or on issues peripherally related to firewalls. Rather, every post (with the exception of the single instance of spam) is aimed both at furthering the goals of the group as a whole by amassing a body of information on firewalls and in assisting individual participants in their efforts to understand, implement, and maintain firewall technologies effectively. Seen through this sample, in fact, the community appears to undertake its work with a bare minimum of fuss or conflict.
In terms of providing an accurate representation of the newsgroup's community, this randomly chosen sample of fifty consecutive posts has two major limitations, especially when viewed in comparison with the other samples.
First, as is the case with any narrow slice of a large, on-going community, this sample is limited by its arbitrariness. Because it both begins and ends in medias res, the sample necessarily omits both a number of queries that are answered within the sample and, more importantly, a number of replies to queries that appear within it. Thus, the view of the community provided by the sample may be misleading; it is very possible, for example, that one or more of the threads that begin within the sample may have erupted into flame wars in posts following the sample itself, an eventuality that the sample itself could never reveal. Because of this, the sample may miss some of the elements of social interaction that are common within the group, but (for whatever reason) did not occur during the very brief period of time represented by the sample. It seems likely, then, that the sample cannot be easily generalized as representative of the community over time.
Second, the sample misses both the extended interactions of the most active threads and the active participation of the most frequent posters. Thus, it clearly misrepresents the level of commitment of the active posters, and may misleadingly present infrequent participants as if they were more central to the community than they in fact may be. Indeed, a cursory look at the full six weeks of posts gathered for this project reveals that some posters who appear to be core members of the community, posted rarely outside of this sample or (more commonly), even if they did post regularly, could hardly be characterized as active participants. The sample of fifty consecutive posts provides no way of assessing such situations.
This sample gathers the five threads with the greatest number of postings found during the period in which the data were collected. While we discuss only one of those threads in detail, analyses of the other threads revealed similar characterizations.
The thread included thirty-four postings from a total of twelve individuals, who include Europeans (probably British and French) and Americans; more than likely, all participants were male. References in the text suggest that the ages of participants may be widespread.
The poster who started the thread asks for a firewall solution to consistent attacks on a Web server, both from hackers and viruses. Five posters offered help, but the bulk of the messages comprised a flame war between two posters who are self-proclaimed firewall experts. Another poster offers solutions at times, but also negotiates expertise with some of the other posters.
Throughout the thread, posters snip entire texts from previous messages as a way to provide coherence. The extensive use of snippets reflects the way in which Usenet messages are received, often not in chronological order, and sometimes twice. In several instances, however, they also snip partial message texts, either to fuel a flame war and/or to inject humor, as in this example text, which attacks the first poster's expertise by insinuating that he works in a fast food restaurant rather than in computer security:
I got to go to work. Have fun flipping the burgers.
In this sample, grammar rules were consistent with the other samples. Fifty percent of the posters were blatantly anonymous, about a third used an e-mail address designed to protect them from spam, and over fifty percent used some type of signature file. Several postings refer directly to communication norms, as in one example that reminds others to avoid cross-posting to other newsgroups: 'Try not posting to every group under the sun.'
Outside references allow us to characterize the nature of work for firewall experts. From references made in the postings, we learn which software is being used to prevent and detect intrusion, and which alternatives are favored or disdained in the community. We learn about viruses that concern these experts, e.g., CodeRed. From the community, we can construct a list of companies and resources that can inform us about firewalls and security. In this particular thread, we learn that there is dissension in the community about whether BlackIce is a firewall at all, and whether it is appropriate for commercial use. We learn that a GRC Leaktest is something that firewall experts do. We learn that most firewall experts who consider themselves to be gurus run command line interfaces, not graphical user interfaces, on their Web servers:
but then again I couldn't see why one would want to run a GUI on a server (most of the time I might add) at all. ;)
The format of the thread lends itself well to an analysis of invention in the text. In the thread, a query was posted, including technical elements of a current problem, which illustrates 'speaking from the past'. The responses 'speak the present' by offering new solutions. The rest of the postings negotiate the new solutions, 'speaking the past' by referencing previous texts, but also 'speaking the present' by offering alternative perspectives.
The content of the messages reveals several intentions. The initiator of the thread had the intention of asking a question. Several posters intended to answer the query, as in this text:
There are two alternatives I can think of: Get all the current patches from MS and apply them. Hope that there are no new major security holes waiting to be exploited. Given IIS's security record you will most likely be unlucky. Get Apache for Windows and run it instead. It has a much better security track record than IIS. Obviously, problems will arise so, again, make sure you stay up to date with any security fixes.
Other posters intended to demonstrate their own expertise about firewalls and security, and discredit the expertise of others. This intention was illustrated predominantly in the flame war that ensued, but also in attempts to diffuse flaming. During this flame war, several posters make explicit knowledge claims, while others refute those claims. When the knowledge claims differed, then attacks on reputation (or expertise) began as the following post illustrates:
Just what is it that you do for a living. Are you in the IT field doing network security, operations, pc tech, programming, operations, systems? Or is it none of the above?
This poster indicates that he does not respect the other's expertise, and with his laundry list of IT positions, tries to demonstrate his own expertise at the same time.
Such interaction suggests a strong newsgroup norm that does not tolerate lack of expertise. Ignorance about firewalls and security is taken as ignorance in general, and any demonstration of lack of knowledge results in attacks on the poster. The threads with the greatest number of postings portray a very hostile environment in which to build a knowledge base, inaccessible to newbies.
Our analysis of the five longest running threads during the sample period revealed two related characteristics. First, knowledge creation, the ostensible work of the community, happens on the edges of the discussion. Second, frequent posters negotiate their reputations as firewall or security experts. In several instances, posters would post a single message offering a solution to the query, and then drop out of the thread, choosing not to participate in the flame wars that ensued. One poster, for example, snips heavily from the original message and intersperses his on-task response in this single message:
[original poster's text about being hacked and having viruses] Probably CodeRed or Nimda. [What can I do about prevention?] Do the first thing an admin should do: keep your software up to date! Patch your 2k box !
This poster does not reappear in the thread.
In contrast, frequent posters spend their time negotiating reputations, not offering any real solutions, as earlier quotes from the thread suggest. The postings are not substantive in terms of knowledge creation. So at least in the longest running threads, we have to sift through a great deal of 'I know more than you know' to find out something that someone might actually know.
As this analysis suggests, the longest threads do not necessarily reflect the true work that takes place within the newsgroup, but rather emphasize the negotiation of reputations that take place by flaming and social sniping. Indeed, looking at long running threads reveals a limitation of the conceptual model. Communication frequency did not necessarily correlate with the amount or quality of work being accomplished. Our model does not explicitly capture the importance (or unimportance) of communication frequency.
In this section, we provide short profiles of each of the five most prolific posters. During the period studied, these five individuals contributed 400 separate posts to the group. Each of these individuals has a unique profile, with differentiating characteristics ranging from their use of signature files and emoticons to their areas of expertise. All appear to be male, although that cannot be determined with certainty.
During the period of study, the first prolific poster made 154 posts to the newsgroup. He uses no signature file, uses a pseudonym for all of his posts, and has modified his e-mail address to combat spam. The second prolific poster, who uses his full name for posts, uses his correct e-mail address, and has no signature file, made 94 posts. The third poster made 65 posts during the period of study, using his first name only, and providing his correct e-mail address and no signature file; unlike the other active posters, he never uses salutations or closings of any sort in his posts. The fourth poster, who also uses his name and correct e-mail address, consistently uses a signature file (quoting a popular song) in his 55 posts. The final active poster also uses a signature file throughout his 32 posts, in which he modifies his e-mail address in an explicit effort to combat spam; he also, alone among these five, has an e-mail address which uses his own domain name.
During exchanges that focus on firewall technology, each of the five posters maintains a consistent approach to structuring messages, snipping short segments from previous posts to provide a context for their answers, or, for more complex questions, interpolating answers into the middle of longer quotes. However, this pattern breaks down when something goes 'wrong' in a thread, whether because a post betrays lack of knowledge or expertise or because a post challenges the expertise of the prolific poster. In these cases, each of the five will avoid answering the content of the previous post, and address the perceived ignorance or threat.
In addition, each of these prolific posters includes small, personalized touches within their posts which, though they may not closely follow the newsgroup's norms for message coherence, serve to identify them as individuals. For instance, one of the five uses emoticons in his posts, something that is rare elsewhere in the group. Similarly, this poster, like one other, includes an automated preface to anything he quotes from other participants:
"Taking a moment to reflect, [poster's name here] wrote:"
Interestingly, there does not seem to be a correlation between the sheer number of posts made by an individual and the breadth of community knowledge generated by that individual. Indeed, the most active of the five posters responds only to posts that refer to the firewall product ZoneAlarm in their subject lines, while another tends to post in a variety of threads (often multiple times) only to denigrate other community members and, even, firewall technology in general, as in one post in which he writes, simply:
Personal firewalls are unnecessary crap.
Only two of the five most prolific posters post on a wide range of firewall topics, although one of them posts much more frequently when the discussion involves a particular product.
One of the posters writes straightforward answers to even the most naive of questions on a variety of firewall topics, and occasionally acts as peacekeeper. For example, in one exchange, he keeps the group on-task by responding to a flaming dismissal of a firewall as 'braindead' by writing:
I disagree. It can make sense to use both. They might already have a central firewall, the poster didn't say.
While the previous post used reference as an excuse for argument, this response returns the group to a focus on issues related to firewalls, thus maintaining shared reference as a tool for community building.
Posts of the prolific posters are highly self-contained, and display little explicit relationship to associated texts; rather, they tend to draw upon their own firewall expertise to answer questions. If one of the five posts more than once in a particular thread, he will on occasion refer to his own posts. In one case, one of the prolific posters refers a newer member of the community to a different thread, which presumably contains relevant information. Also, as noted above, the five prolific posters tend to draw upon their own personal experiences with specific firewall technologies; thus, they tend to 'speak the past' of their own existing knowledge. The information they provide to others, however, may 'speak the present' for the group as a whole, adding to the collective body of knowledge in ways that are otherwise unlikely.
The prolific posters' posts reflect several intents in their postings. Mostly, they provide help, assert their knowledge, maintain their reputations, flame others, or attempt to keep the peace. Of some interest is that their pay-off for doing so is not apparent in the text. That is, it is apparent from the texts that they are protective of their knowledge, expertise, and reputations, but it is not clear how they personally benefit from that protection other than maintaining a high profile within the newsgroup.
Prolific posters do not contribute heavily to on-going threads, but rather tend to post only once or twice within a thread. The five most prolific posters in this community rarely interact directly with one another. Instead, they answer questions posted by less frequent posters, offering advice and help and at the same time working to keep their own presence and expertise in others' awareness.
The most prolific posters almost never start threads or ask questions. One of the five begins two new threads within this sample; the other four start none. When these prolific posters, who all consider themselves experts in some aspect of computer firewall technology, do ask questions, it is generally not to gain information that they can use outside the list. Instead, they ask questions for two reasons: first, to clarify someone else's information need; or second, to denigrate someone else's knowledge, as in the following example:
I have been in the IT field since 1971 from the mainframes to the client server platforms. I have forgotten more about things in this industry then [sic] you will ever possibly know.
The five prolific posters, on rare occasion, do exert their power (or their perceived power), acting as arbiters of Usenet or newsgroup, for example reminding other posters to avoid using HTML in their posts or recommending more effective subject lines, as in the following example:
Maybe you need to repost with a different subject like 'ZA and FTP issues.' You should be able to find some good ZA people here.
This slice of the data analysis leaves us with no good way to examine or understand how these five prolific posters contribute to each thread or to the culture of the newsgroup as a whole. With the focus on individuals rather than on group-wide interactions, our view of knowledge creation lacks context, in part because we are unable to see how the texts produced by the five prolific posters are taken up or interpreted by others. Rather, this sample only allows analysis of the ways in which the five individuals explain, clarify, or enhance their own contributions. Thus, while these five posters are highly visible and significant members of the community, a sample that examines only their contributions risks a seriously distorted view not only of the community as a whole, but also of the social role played by the highly active posters.
Unlike the threads used in Sample Two, none of these threads persist for more than thirteen posts, although all of them continue over a period of several days. In our original formulation of the methods for this project, we had not anticipated using such a sample, assuming that analysing longer threads and more active participants in addition to the original set of fifty consecutive posts would provide a good overview of the activities of the newsgroup. However, our examination of the other samples led us to suspect that, while posts to the longer threads were often less than substantive and the posts by very active posters often tended to reflect their own idiosyncratic interests, the primary work of the group might take place elsewhere. Since we had observed that the majority of threads were, in fact, quite brief, it was decided that a fourth sample should be drawn to test our suspicion. As this analysis will demonstrate, the fourth sample tends to corroborate this suspicion.
All of the five short threads in this sample follow a common pattern. Each begins with a single post that describes a situation and asks for assistance or for further information. Most subsequent posts in each thread attempt to provide answers, although (in two cases) some discussion takes place debating the details of those answers. Three of the threads reach a conclusion that is satisfactory to all participants (i.e., the initial question is answered), while two of them simply come to an end without full resolution. The final post of the shortest thread (of only three posts) gives some indication of the seriousness with which participants engage in their interactions:
Between [the first] response and mine, I hope we have answered all your questions fully.
By contrast, the longest thread, which unfolds over seven days through thirteen separate posts (two of which are duplicates), ends with some degree of ambiguity in the answer. While all of the posts directly address the initial query, participants disagree about the details of the answer, and engage in some back-and-forth about those details. However, even this thread ends with an acknowledgement that the answers put forth by all participants are of value in the overall goal of helping the initial poster find an answer; the final poster states his disagreement with earlier posts, but concludes by noting that his 'Knowledge ... is limited, so [he] could be wrong'.
Such dialogue is typical of the short threads, even one in which all posters beyond the first make it clear that they think the initial question (about ways in which to sidestep an employer's security measures) raises ethical issues. All of the posters to this thread note those ethical concerns, but still attempt to provide serious answers while warning the original poster that he may find himself 'up a creek' and without a job if he disregards their warnings. Even here, the full focus of all participants is on issues related to firewalls rather than personalities or reputations.
The elements of coherence described in our analysis of the other samples pertain within the five short threads as well. Here, as elsewhere, it is clear that strictly structural characteristics of posts, such as placement and extent of quotes, can either impede or enhance the communicative and informational interactions of the group, depending upon how closely the norms governing them are followed.
The objects and activities to which the posts in these five brief threads refer, as in our other samples, remain sharply on task. Not surprisingly, because of the brevity of these threads, and because of the degree to which they focus on problem-solving and question-answering, the range of references in each thread remains narrow, and each thread is limited to a single reference, though most of the threads explore several aspects of that reference.
Each of the five threads reaches a conclusion through the creation of new information intended for the use of the community as a whole.
Again, because of the brevity of the five threads in this sample, issues of intention are quite straightforward. In one case, the difficulties of assessing the intentions of another becomes an explicit concern for one poster, who writes:
I'm not sure whether you're most probably referring to *SSL* vs. VPN, and not SSH.
While it ultimately becomes clear that the initial poster was, in fact, referring to SSH rather than SSL, the potential for ambiguity in both questions and replies becomes a focus for the remainder of the thread. Relationships among the three technologies become the focus of the discussion, with the result that the body of knowledge created by the end of the thread becomes much richer than the initial questioner intended. In this sense, the intentions of the group are reflected in their interactions. Thus, and in a fundamental regard, intention becomes retrospective: while the initial poster did not have all of the aspects of the ultimate discussion in mind when raising his question, the processes through which others in the community interpret the texts that precede theirs create not only their own understandings, but effectively recast and broaden the intentions with which the thread begins.
Like the first sample of fifty consecutive posts, this sample paints a picture of a group that is atypical of Usenet as a whole. The five threads of this sample are consistent in their sharp focus on issues related to firewall technologies. Even those instances in which other issues are raised; the use and placement of quotations, for instance, or the intended meaning of an earlier post, are done in such a way that the priority remains firewalls; the group represented by these threads does not allow itself to be distracted by endless flame wars or other meta-conversations, as happened in the longer threads.
Because of the brevity of the threads within this sample, it does not give a clear picture of the full range of the interactions that take place within the newsgroup. For example, only two of the most active posters appear within these five threads. Further, the sample makes it appear that some posters are more active within the newsgroup than they are outside of these five threads. For example, in one thread a single participant makes three posts compared to one by another participant. Further examination reveals that the active poster in this thread is only moderately active elsewhere in the group, while the other poster is (while not one of the most active) very active in discussions of the specific technologies with which he is most familiar, and could be considered a core member of the community. A sampling of only brief threads, while it does reflect the level of on-task interaction that they contain, is thus limited in both scope and representation of individual participants.
This study is an initial attempt to illustrate how language use both reflects and influences culture in a virtual community using an approach based in cultural hermeneutics and textual analysis. The four elements of our conceptual model: coherence, reference, invention, and intention, provide a set of entry points for examining the texts exchanged by a virtual community as they go about their daily business of text-based social interaction and knowledge creation. Using a specific community, a Usenet newsgroup devoted to firewall technologies, for our analysis, this pilot study aimed to test the usefulness and applicability of the four concepts for understanding virtual communities. Four separate samples were used to focus our discussion and to reflect the variability of participants' views of virtual communities that make up Usenet; this approach, in essence, has allowed us to conduct a multi-faceted case study of a specific community in addition to testing our concepts in practice.
While the findings of a case study—even one as multi-faceted as this—cannot easily be generalized to other situations, the findings of this study suggest a number of important conclusions that should be applicable to other communities.
First, while it has often been observed that information exchange and socializing are intertwined in virtual communities (see, for example, Burnett, 2000), the four concepts allow a robust understanding of the relationship between the two. By focusing on the formal characteristics of a community's texts, the concept of coherence allows us a greater understanding of the ways in which such characteristics are not only socially derived, but also of the ways in which they enter directly into the discourse of a community and can be consciously used by the community to enhance efforts to create a community-based body of knowledge. For example, the reminder made by one of the five most prolific posters to use accurate and appropriate subject headers reflects the community's awareness that formal textual elements of their posts have an impact on the ways in which they can be interpreted by other community members. While other communities may integrate their awareness of textual elements in their own idiosyncratic ways, we would suggest that such awareness is, most likely, a common feature of virtual communities.
Second, the concept of invention makes explicit the ways in which communities can use texts to 'speak the past' by using existing texts in a social setting to help define the current state of knowledge within the content realm chosen by the community as its own. Conversely, it also makes clear the ways in which communities, through social interaction, both adapt existing knowledge to their own purposes, making it relevant within their own specific context, and 'speak the present' by producing new knowledge that meets their own specific needs. Our study, focusing on one community's activities over a period of six weeks, illustrates that community's unique approach to the mechanisms of invention. Again, while other communities will be quite different in the specifics of their knowledge invention, we suggest that the concept has the potential to allow a new and more robust understanding of socially-based knowledge structures in virtual communities.
Finally, a focus on the multiple dimensions of texts provides a new understanding of the full importance of texts within virtual communities. Our analysis suggests that texts are not merely vehicles for communication, not, that is, simply conduits for the unambiguous transfer of information from one person to another, but rather serve multiple purposes simultaneously. While they do transfer information, they also provide that information within a social context, and create an expanding archive of socially-contextualized information well beyond the capabilities of any individual participant. In turn, this allows groups to negotiate reputations, socialize, and define the limits of their knowledge.
As noted above, this study allowed us to uncover an important limitation of the conceptual model. Our analysis of the longest threads suggested that knowledge creation was a direct result of neither frequency of posting nor the length of a given interaction; indeed, the relationship between the two may be negative: as threads in the virtual community became longer, they tended to diverge from the work of the community, becoming more and more enmeshed in flames and personal/professional antagonisms. While the conceptual model allowed us a robust understanding of the community, future applications of the model will need to integrate this understanding, and find a way to account for this discrepancy.
Another limitation is that this pilot study involved a virtual community that relied totally on a single type of electronic communication for its interchanges—postings to a Usenet newsgroup. Many virtual work groups and communities rely on multiple media, such as telephone and e-mail, and sometimes even face-to-face communication for their exchanges. It remains to be seen whether our approach provides sufficient robustness for understanding culture in situations where multiple communication channels are used.
Using knowledge gleaned from our pilot study, we will revise our model and use our ideas to examine less amorphous online settings such as organizationally-based virtual environments. We anticipate that the current study will lead to an on-going series of such studies, which will result in a rich understanding of the textual dynamics of online communities as well as of the role of text in creating information stores in those communities. Thus, our work has important implications for developers of online communities and for organizations that use online environments to conduct work. We anticipate that our work will result in a series of recommendations for the design and management of online work environments that can optimize the effectiveness and usability of those environments while minimizing the kinds of distractions the current study observed in the longer threads.
This study is an initial attempt to illustrate how language use both reflects and influences culture in a virtual community using an approach based in cultural hermeneutics and textual analysis. Our pilot study analysed contributions to a Usenet newsgroup on firewall technology by using elements in our conceptual model to examine the community's texts as it engaged in social interaction and knowledge creation.
While it is generally accepted that information exchange and socializing are intertwined in virtual communities, our model allows a robust understanding of the relationship between the two. Invention makes explicit the ways communities use texts to 'speak the past' in social settings to define the current state of knowledge. Conversely, communities adapt existing knowledge through social interaction to make it relevant, and 'speak the present' by producing new knowledge to meet their specific needs. Focusing on multiple dimensions of texts provides a new understanding of their full importance within virtual communities. Texts serve multiple purposes simultaneously and are not merely vehicles for communication. Concurrently with the transfer of information, texts also provide this knowledge within a social context, and create an expanding archive of socially-contextualized information well beyond the capabilities of any individual participant. This allows groups to negotiate reputations, socialize, and define the limits of their knowledge. This study demonstrates that our conceptual model can provide the foundation for a richer understanding of culture in virtual environments that rely on text-based communication for their interaction.
| Find other papers on this subject. |
| ||
© the author, 2003. Last updated: 18 September, 2003 |