Managing and evaluating personal reputations on the basis of information shared on social media: a Generation X perspective
Introduction
This paper presents preliminary findings of an investigation into how online information is used in the management and evaluation of personal reputations. Here the term ‘personal reputation’ refers to the reputation of private individuals, rather than corporate identity and brand. Two broad research themes are considered: (1) the means by which individuals evaluate or assess the personal reputations of others from the online evidence available to them and (2) how individuals manage (for example build and maintain) their own personal reputations through their use of online information, and to the extent to which this behaviour is intentional. These findings contribute to a larger doctoral study that follows the tradition of research into everyday life information seeking (ELIS) (Savolainen, 1995). As such it addresses four research questions as listed in Table 1 below.
Although the study aims to investigate general online information use and practice in the building and assessment of personal reputation, its scope is limited to three widely used social networking platforms: (1) Facebook; (2) Twitter; and (3) LinkedIn. These sites were determined on the basis of the top ten sites and apps identified in Ofcom’s 2014 Adults’ media use and attitudes report (Ofcom, 2014, p. 39), as well as participants’ apparent levels of engagement with the platforms.
For the purpose of this paper, identity is broadly understood as the representations of self/selves that individuals create for or about themselves, based on the works of Goffman (1959), Bullingham and Vasconcelos (2013), Rodogno (2011), Uski and Lampinen (2014), and van Dijck (2013). Information is regarded as any tangible ‘object’ that can be accessed and viewed online, using Buckland’s concept of ‘information-as-thing’ as the guiding principle (Buckland, 1991, pp. 351-360). The personal opinions and character judgements one individual has for another comprise reputation. This is a definition that is common in other domains (Casare and Sichman, 2005; Morris, 1999; Origgi, 2012). Social media in this context refers to computer-mediated communication technologies that are typically used to connect people with one another, as well as to produce and share user-generated content. These include social networking and microblogging sites, wikis, forums, and blogs (Osatuyi, 2013, p. 2622). Social networking sites are Web-based services that allow individuals to (1) construct profiles within the system, (2) view lists of other users with whom they share a connection, and (3) view and traverse their list of connections and the connections of others within the system (Boyd and Ellison, 2007, p. 211).
The findings discussed here are prefaced by a literature review. This considers published work (where it exists) on the role of information in personal reputation management and evaluation. It draws on (1) a broad collection of papers from a wide range of subject domains, the content of which has a bearing on the main themes of the work in progress, and (2) an established and focused research stream in information science on the building of academic reputations through citation practices. Attention then falls on the research approach adopted for the study. This takes into account common practice in everyday life information seeking studies, and how the data for this study have been analysed thus far.
The findings to date reveal that individuals use online information to manage their reputations to some extent – even if they are not consciously aware of their actions – and that they deploy a range of tactics and behaviour in doing so. Equally, there are indications that online information is used to evaluate the reputations of others, even if those who make the evaluations are not actively aware of their practice. This has implications for the way in which we consider human information behaviour as it relates to everyday uses of online information, highlighting that online information has an impact on the management and evaluation of personal reputations.
Literature review
The interdisciplinary nature of the research themes of this study means that much of the relevant academic literature is dispersed across a number of subject domains. Areas of investigation include: the impact of social media use on employment and human resource matters (Fieseler, Meckel, and Ranzini, 2014; Foste and Botero, 2011; Labrecque, Markos, and Milne, 2011; Madera, 2012; Roberts and Roach, 2008); personal branding and identity strategies (Fertik and Thompson, 2010; Harris and Rae, 2011; Karaduman, 2013); personality traits and characteristics (Kluemper and Rosen, 2009; Moore and McElroy, 2012; Suler, 2004; Yue, Kan, Xiaomeng, and Zhen, 2010); seeking and sharing information about physical or mental health issues or topics that may have negative stigmas attached (Greidanus and Everall, 2010; Harviainen, 2014; Lingel and Boyd, 2013; Marciano, 2014; Mesch, 2012; Răcătău, 2013); the quality and accuracy of information and individuals’ right to be forgotten (Ausloos, 2012; Craig and Ludloff, 2011; Dennis, 2013; European Commission, 2010; Finocchiaro and Ricci, 2013; Tsikerdekis and Zeadally, 2014); and personal identities and the use of ‘real names’ online (Boyd and Heer, 2006; Boyd, 2011, 2012; Bullingham and Vasconcelos, 2013; Clear, 2014; Giles, 2011; Lund, 2012; Renninger, 2014; The Government Office for Science, 2013; Wessels, 2012).
A further challenge of the literature is that evidence of how general personal reputations are evaluated through the use of online information is weak. There is some published research that considers how individuals’ social media ‘footprints’ are evaluated for employment and human resources purposes (Kluemper and Rosen, 2009; Labrecque et al., 2011; Madera, 2012). However, these approaches are not systematic, and the area of evaluation appears to be under-researched. At the same time, there is work which considers aspects of individuals’ reputations such as professional personas (Fieseler et al., 2014). However, there are gaps in the knowledge relating to the larger, whole-person picture, where information from a number of sources can be aggregated for reputation management and/or evaluation.
In addition to traditional academic literature, an examination of non-academic sources – for example current news stories, as well as reported trends in social media use – was undertaken in preparation for the empirical stage of this study. Such sources (for example: CNN Living Staff, 2013; Goodman, Cherubini, and Waldhorn, 2013; Peters, 1997) confirm that topics related to information seeking behaviour and personal reputation management are of interest to a range of professionals. These include those working in human resources and reputation management, social media practitioners and platform owners, and managers of online platforms and social networking sites. General members of the public, including users of social media platforms, are interested in these themes too.
There also exists in the domain of information science an analogous stream of academic literature on the role that information (both off-line and online) plays in the management and evaluation of personal reputations. This is the extensive body of work on citation analysis (or scientometrics), which stretches back to the mid-1960s (Cronin and Atkins, 2000, pp. 1-6). Citations build researchers’ identities and reputations, and increase their visibility among peers (Cronin, 1985; Cronin and Atkins, 2000). Their impact is also felt by both the those who give citations and those who receive them (White, 2001). As illustration, Table 1 summarises practices discussed in the citation analysis literature and related behaviour evident in social media practices.
| Research questions | Theme | Practices discussed in the citation analysis literature | Related behaviour evident in social media practices |
|---|---|---|---|
| RQ1: How do individuals create identities for themselves online? |
Linking or connecting with
other individuals as a means of showing agreement or similarity |
Citing someone within the main
content of a paper (Cronin and Shaw, 2002b; Ding, Liu, Guo, and Cronin,
2013; Hyland, 2003; White, 2001) Making note of someone in acknowledgements or footnotes of a paper (Cronin, 1998) |
Favouriting or liking a post Sharing or retweeting a post Individuals link their content to that of others Mentioning individuals via user names Hosting or providing guest blogs |
| Self-promotion | Self-citation (Costas, van Leeuwen, and Bordons, 2010; Cronin and Shaw, 2002b; Hyland, 2003; White, 2001; Wilhite & Fong,
2012) Sharing details of work on social or professional networking sites or other online platforms (Costas, Zahedi, and Wouters, 2015) |
Individuals link to their own materials on the pages of
others Cross-linking or cross-posting of materials across several platforms |
|
| Strategic placement of materials in favourable locations | Agreeing to coerced citations (Wilhite and Fong, 2012) Citing well-known authors in specific fields of study (Cronin, 1998) |
Participation in blogs and online communities | |
| Connecting with individuals to boost own reputation | Citing well-respected authors (Cronin, 1998) Following academics on networking platforms (Cronin and Shaw, 2002a) Co-authoring papers Providing ‘gift’ or other honorary co-authorships (Cronin, 1998) |
Friending, following, or otherwise connecting with individuals | |
| Fraudulent practices or identity masking | Coercive self-citations or other citations added at the request of a publisher or editor (Cronin, 2001) | Use of anonymous accounts Use of pseudonyms |
|
| RQ2: How do individuals use online information to create and manage their reputations? |
Linking or connecting with other individuals as a means of showing agreement or similarity | Citing well-respected authors
(Cronin, 1998) Following academics on networking platforms (Cronin and Shaw, 2002a; Lupton, 2014) Co-authoring papers with well-respected academics (Cronin, 1998) |
Linking to well-respected bloggers Connecting with others through ‘mentions’ Re-posting content of others Providing or offering guest blogs |
| Self-promotion | Self-citation or otherwise referencing previous works by
one’s self (Costas et al., 2010; Cronin and Shaw, 2002b; Hyland,
2003; White, 2001; Wilhite and Fong, 2012) Sharing through social media platforms (Cronin, Snyder, Rosenbaum, Martinson, and Callahan, 1998; Lupton, 2014) |
Linking back to own content on other platforms Sharing information from one platform on another |
|
| Strategic placement of materials in favourable locations | Sharing through social media platforms (Costas et al., 2015; Priem, Taraborelli, Groth, and Neylon, 2010) | Sharing through social media platforms | |
| RQ3: How do individuals evaluate the identities and reputations of others based on the information available to them online? |
Evaluating the connections of others to determine their reputation | Reviewing list of contacts on networking platforms (Priem,
Taraborelli, Groth, and Neylon, 2010) Reviewing reference lists in articles (Cronin et al., 1998) |
Reviewing social media activities of connections Reviewing lists of connections |
| Evaluating individuals based on their overall visibility | Reviewing citation indexes (Cronin, 1998) | Reviewing online footprints | |
| Assessing individuals based on how they use social media | Too much online self-promotion can be seen as egotistical
(Hyland, 2003; Lupton, 2014) Self-promotion can lead to questions about the oversimplification of work (Cronin and Crawford, 1999) Senior academics forming cliques on social media can be seen as exclusionary towards more junior academics (Cronin and Meho, 2008) |
Sharing a high frequency of information about a single
subject Sharing too many times in a single day Bragging or ‘humble bragging’ on a regular basis |
|
| RQ4: To what extent do individuals actively practise identity and reputation building and assessment online? |
Social media use and promotion | Use of social networking platforms (Cronin et al., 1998; Lupton, 2014) Distributing information through social networking platforms (Cronin et al., 1998; Lupton, 2014) |
Use of social networking platforms Sharing information through social networking platforms |
The findings of the literature review identified a number of further questions to address in this study of the role of online information in personal reputation management and evaluation. In Table 2 these are matched thematically with the four main research questions and show where there are opportunities to extend knowledge in the domain. Whilst the existing literature regarding online information and reputation management is dispersed across a number of disciplines and domains of enquiry (including citation analysis) there remains a lack of in-depth research specific to the interests of this paper and to the larger doctoral investigation on the same topic. It is therefore worthwhile investigating personal online reputation management from an information perspective. This brings new insight to the field of information science, notably related to (1) information behaviour use and (2) digital literacy.
| RQs | Questions raised | Level of coverage in the extant literature | Opportunities to make a contribution? |
|---|---|---|---|
| RQ1 | How do individuals manage
online information regarding their combined professional and private
reputations as one ‘personal’ reputation? How do individuals decide how to represent their identities on online platforms? |
Limited Individuals use self-regulation techniques to manage the information that they will share, and with whom they will share it. Individuals share different types of information on different types of platforms. Individuals manage information sharing and connections specifically for the blurring (or separation) of their private and professional lives. Individuals might use pseudonyms and anonymous accounts to ‘experiment’ with personalities or identities online. These may, or may not, be linked back to an offline identity later. |
Yes – no prior academic studies
have focused on individuals’ ‘whole’ lives in regards to managing
online information; previous studies have concentrated on a single
aspect of individuals’ lives or identities (such as professional lives). |
| RQ2 | How do individuals decide what
information to share online, and where to share it? To what extent do individuals intentionally engage in reputation building? |
Limited Individuals manage reputation by masking or hiding activities or personal information for the purposes of seeking or sharing information. This is achieved using pseudonyms and anonymous accounts, or by deliberately not providing profile information on platforms. |
Yes – prior academic studies
have concentrated on information sharing as it pertains to a single
aspect of individuals’ lives (such as professional identities or
information seeking for specific interests), and have not focused on
individuals’ ‘whole’ lives. |
| RQ3 | To what extent are individuals evaluating the reputations of
others based on the information found about them online? To what extent does the quality of information collected influence the determination of individuals’ reputations? How does offline knowledge of an individual influence the evaluation of information gathered about them from online sources? |
Limited The quality and accuracy of information influences reputation evaluations, as does information that is outdated and no longer accurate. Those with whom individuals are directly connected can influences their reputations, as can their second-level connections. |
Yes – no prior academic studies
into the reputation evaluations of individuals’ own connections;
previous studies have been based on professional evaluations, such as
those by human resource practitioners. |
| RQ4 | To what extent do individuals
actively monitor their online footprints for the purpose of personal
reputation management? If so, how and to what extent? To what extent are individuals aware of the impact that their online activities have on their whole world persona? |
None | Yes – no prior academic studies
have been conducted on this theme. |
It has been established that the means by which individuals build and assess identity and reputation through academic citation practices can be aligned to some aspects of social media use and practice. Importantly, however, there are also key differences. In the case of citation practices, for example, many of the activities undertaken by academics appear to have a direct impact on the building of identity and reputation of other academics, as well as their own. However, the same does not appear to be the case with social media deployment. Here there tends to be a strong practice of creating information regarding individuals’ own identities and reputations, whereas it is apparently uncommon to link to content created by others. The empirical study described below addresses this and other related questions.
Methods
Studies of citation practice tend to favour quantitative research approaches (for example: Cronin and Shaw, 2007; Sugimoto and Cronin, 2012, 2013). Just a few can be found that include qualitative methods (for example: Hyland, 2003). The limited number qualitative studies, including those investigating the motivations behind a citing author’s referencing behaviour, has been noted in the past as a central problem of bibliometric studies (Cronin, 2000, p. 447).
Researchers who investigate social media practices and everyday information behaviour and use are drawn to qualitative research methods. This is because they seek to answer questions about individuals’ motivations, and the reasoning for their actions. As the purpose of the larger doctoral investigation from which this paper derives is to determine how and why participants use online information to build and assess identity and reputation, it is appropriate to use these same qualitative methods.
Therefore, this qualitative research draws upon methods used in everyday life information seeking studies with the use of participant diaries and in-depth, semi-structured interviews. This method was selected after evaluating the practical and ethical implications of other options. The decision was supported following a successful pilot study that tested the appropriateness the approach (as discussed in detail in Ryan, Cruickshank, Hall, and Lawson, 2016). An overview of the data collection process is shown in Figure 1.
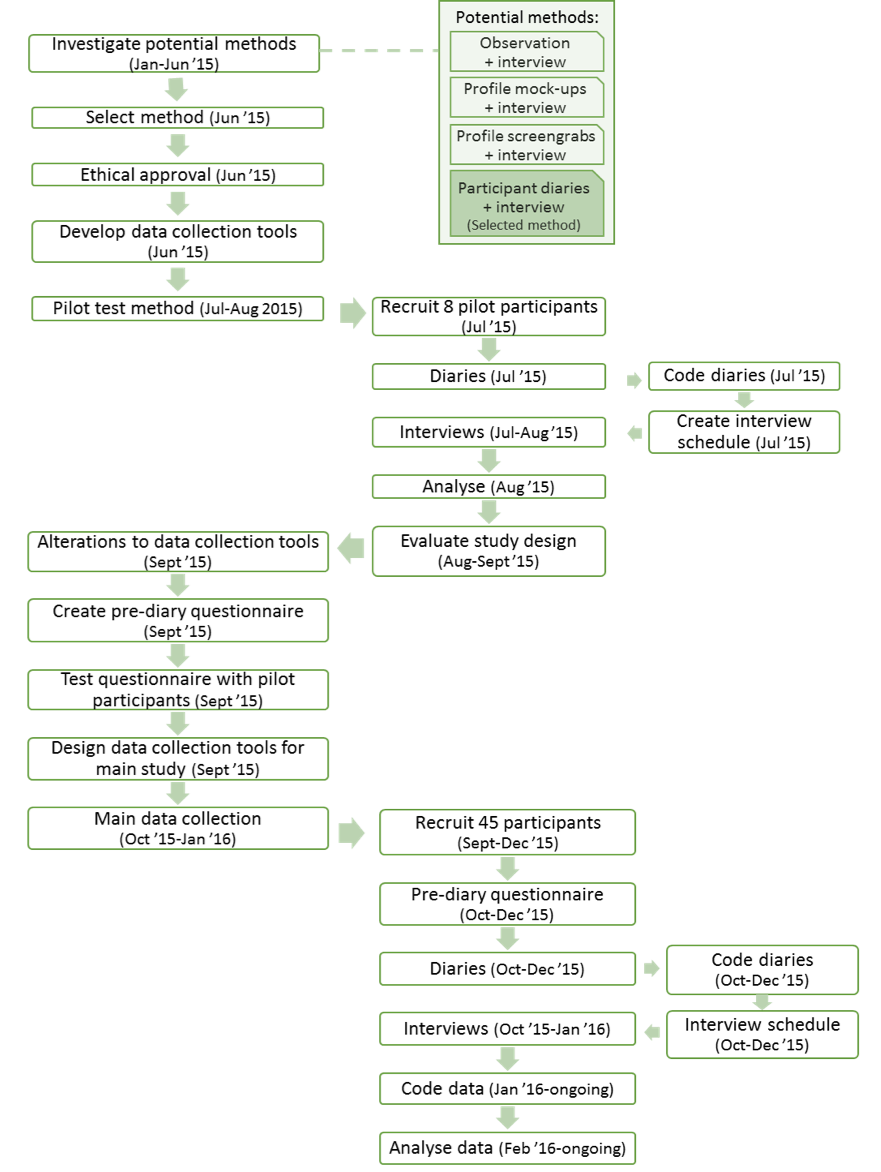
Figure 1: An overview of the data collection process
The study participants are social media users located within the UK. The full data set includes forty-five participants aged 18-69 in groups of 15 from: Generation Y (born 1981-97); Generation X (born 1965-80); and the Baby Boomer generation (born 1946-64). Forty-three participants were recruited through social networking channels including Facebook, Twitter, and LinkedIn, and two were referred to the study through word-of-mouth. No upper or lower limits were set for participants’ levels of social media use. This study met with ethical guidelines and informed consent was obtained for all participants prior to participation.
The findings discussed in this paper are specific to the Generation X subset of 15 participants, the majority of whom are female (13). This small sample poses limitations in discussing gender differences in behaviour. However, it will be possible to explore findings with reference to gender in the larger doctoral investigation.
Details of the Generation X participants, whose information practices are analysed in this paper, are given in Table 3. Levels of social networking site (SNS) use are based on participants’ own assessments. Please note that participant names in the first column are pseudonyms.
| Name | Year (Age) | Gender | SNS use levels | Facebook user | Twitter user | LinkedIn user | ||
|---|---|---|---|---|---|---|---|---|
| M | F | Moderate | Heavy | |||||
| Amanda | 1970 (45) |
|
X | X |
|
X | X |
|
| Gillian | 1977 (38) |
|
X |
|
X | X | X | X |
| Helen | 1965 (50) |
|
X | X |
|
X |
|
|
| Jacqueline | 1966 (49) |
|
X | X |
|
X | X | X |
| James | 1971 (44) | X |
|
X |
|
X | X |
|
| Joanne | 1971 (44) |
|
X |
|
X | X | X | X |
| Karen | 1975 (40) |
|
X | X |
|
X |
|
X |
| Kelly | 1980 (35) |
|
X | X |
|
X | X |
|
| Kevin | 1980 (35) | X |
|
|
X | X | X | X |
| Laura | 1980 (35) |
|
X | X |
|
X | X | X |
| Lynn | 1978 (37) |
|
X | X |
|
X | X | X |
| Michelle | 1978 (37) |
|
X | X |
|
X | X |
|
| Nicola | 1974 (41) |
|
X |
|
X | X | X | X |
| Sharon | 1970 (45) |
|
X | X |
|
X | X | X |
| Yvonne | 1977 (38) |
|
X | X |
|
X |
|
X |
| Totals (average) | (41) | 2 | 13 | 11 | 4 | 15 | 12 | 10 |
Each of the fifteen participants kept a diary for a week in which they logged any everyday information sharing practices observed on social media that they regarded to have an impact on individual reputations. They considered both the practices of others and their own. The diaries that they produced varied in quality and content: some comprised short entries that observed the simple act of sharing or responding to information, whereas others included longer entries with insights into, and suggestions of, motivations that underpin information behaviour.
Having completed their diaries the participants then took part in semi-structured interviews of about one hour in length. A third of the interviews (5) were conducted face to face, and two-thirds (10) by Skype. The interview schedule was developed based on themes and concepts that emerged from the literature review, and the diary entries of the study participants were used as prompts. These themes and concepts relate to the four main research questions and are discussed further in the findings section below. The interviews were recorded and transcribed prior to data analysis and reporting. Short participant surveys were also conducted prior to the diary exercise to collect demographic data and establish levels of social media use amongst the participants.
All data collected were coded using NVivo10 using a coding structure initially based on the themes identified from the literature review. Additional codes were added as they emerged during the analysis of the data.
Findings
The early analysis of data from one of the three generations (Generation X) has focused on (1) developing an understanding of how the practices of the sample relate to the findings of the initial literature review for the study and (2) determining any additional themes of relevance to the four research questions. The data used for this analysis comes from participant interviews, which incorporated themes and entries mentioned in participant diaries. The preliminary findings are presented below, with participant names noted where appropriate.
RQ1: How do individuals build identities for themselves online?
For this group of participants the act of building an identity – or multiple identities – online is based on their offline personas. Their social media use is largely an extension of who they are in their everyday lives. None currently uses anonymous accounts for their social networks. However, one stated that she had used anonymous names for parenting-related forums in the past (Helen). This lack of interest in online anonymity may indicate that participants in this group are comfortable with having an online presence, or that they have had limited needs for online anonymity.
Pseudonyms, however, are of greater interest to the participants: six mentioned them in the course of their interviews. Where pseudonyms are used, they are sometimes created with strong associations to the participants’ ‘real names’. For instance, a pseudonym may be used in cases where real names are not available (for example, because they are already taken), but real names are attached to the account in question. One participant follows this practice because she likes ‘the idea of being consistent and being open about who [she is]’ (Gillian). Another participant uses a pseudonym on Facebook so that individuals from her professional life cannot easily find her, yet the family and friends with whom she is connected know that the account belongs to her (Yvonne). Two participants have used pseudonyms on Twitter in the past before they were comfortable with sharing their ‘real’ identities. However, these were seen as ‘user names’ or ‘nicknames’ rather than unique identities (Amanda; Sharon). One participant uses a pseudonym on her private, locked Twitter account, although her identity is known to her followers (Joanne).
Where there are intentional actions related to the building of identity, these are related to the idea of building a different persona or personality for different platforms or audiences. These are not necessarily different identities however, and are used to distinguish between professional and private roles in individuals’ lives. Only one participant spoke specifically about creating multiple personas, stating that she has two ‘different personas’: one for her ‘personal online presence’ and one for her ‘professional online presence’ (Nicola). These ‘personas’ are created by managing which information is shared with which connections – without altering the ‘whole’ self. Thus, it could be argued that Nicola is not creating a separate identity. Instead, she is using self-censorship techniques across her different social media accounts.
The remaining participants spoke of their identities as singular, but acknowledged intentional behaviour for management of reputation as a way of projecting aspects of their offline identities, rather than the creation of identities.
RQ2: How do individuals use online information to build and manage their reputations?
Two ways by which all participants in this group build and manage their personal reputations are: (1) by managing the way in which their private and professional lives blur and (2) by undertaking some level of self-censorship. Both of these methods rely on limiting access to information for some connections, or taking care with the forging of connections in the first case. Managing the blurring between private and professional lives means that participants must deploy a number of tactics and behaviour. These include one or more of the following: using one platform for the private ‘identity’ and another for the public identity; adhering to rules or guidelines to determine connecting practice on different platforms; or undertaking varying levels of self-censorship across one or more platforms.
In some cases, private and professional lives are kept separate by managing multiple accounts on the same platform. For example, one participant (Joanne) manages two Twitter accounts. One of these is a public account used to connect with both private and professional contacts as a way to showcase her professional personality, with occasional tweets from her private life to share her non-professional personality. A second account is private and she is ‘quite careful’ about who she allows to follow that account. This allows her to be freer in what she shares with a small, select audience, whilst still having a ‘whole person’ Twitter presence for her professional connections (Joanne).
In some cases the means by which individuals build and manage their reputations varies from platform to platform. Twitter, LinkedIn and Facebook are therefore considered separately below.
The six Twitter users from this group who only maintain one personal account (Amanda, Gillian, Jacqueline, James, Kevin, and Sharon) view the platform as public and use the site to communicate professionally. Three (Amanda, Kevin, and Sharon) use Twitter strictly for professional information sharing, whilst two (Gillian and Jacqueline) also share information from their private lives to help build more rounded reputation for their professional connections. For Gillian, this is a natural blurring as she thinks her ‘professional and personal life overlap quite a lot … so sometimes [it is hard] to determine whether [she is] sharing something because of a professional reason or personal reason’ (Gillian). One participant (James) uses Twitter for both his private and professional lives, but is careful to ensure that information he shares from his non-professional life is appropriate for his professional connections to view. This private-professional blur and self-censorship also carries into his Facebook account.
All ten participants who use LinkedIn view the platform as a professional network where private information should never be shared, even when connections are friends in their non-professional lives. With the exception of Yvonne, who accesses LinkedIn at least once per day, participants do not access LinkedIn on a daily basis. Instead, LinkedIn acts as an ‘ongoing live CV’ (Kevin) that is updated when roles change. They are less likely to access the site on a regular basis or to update their profiles unless they know others will be accessing their profile, or they are in the process of seeking employment.
In maintaining a private/professional separation, it appears from the results of this study that it is more important not to share private information on accounts that are intended to portray a professional image. However, fourteen participants are willing to share at least some level of their professional identity on accounts that relate primarily to their private identity (for example, occasional posts about work on Facebook). This one-way crossover is generally based on the sharing of professional information that also has an impact on a participant’s private life. There is one participant (Kelly) who will not share professional information on her private accounts ‘because it is recorded, it’s there for people to see and to refer back to’ and that makes her ‘uncomfortable’ (Kelly).
All fifteen participants consider Facebook to be a platform for their private lives. However, they all demonstrate a level of professional blurring by connecting with a select set of professional contacts, and/or share limited information about their professional lives on the platform. Here, the motivations behind information sharing behaviour vary greatly, but share a common theme in the form of self-censorship or selective sharing: all noted that they are careful about sharing certain types of information. They all avoid sharing anything that they deem too ‘personal’ or ‘private’, although participants have different ideas about what personal or private information means. For example:
- Amanda will not share information about her husband and children or her political and religious views (Amanda);
- Gillian avoids posts that include political commentary or sexuality (Gillian);
- Jacqueline will not directly share information about sexual orientation or lesbian, gay, bisexual, and transgender issues (Jacqueline);
- Helen avoids sharing anything that indicates she might be having ‘a really bad day’ (Helen).
Three participants (Jacqueline, James, and Karen) avoid sharing anything on Facebook that they think their connections would find ‘boring’. For Jacqueline this means she will not share all of her cycling achievements (Jacqueline), for James it means he avoids sharing too many posts about his day-to-day work activities (James), and for Karen it means not sharing too many photos of a single activity (Karen).
All fifteen participants view themselves as very aware of the information that they are sharing, although they do not feel that they are always thinking about their reputations when sharing information. Nine participants are more likely to consider whether their Facebook connections will find the information ‘funny’ or ‘interesting’, rather than wondering if others will evaluate their reputations as funny or interesting. However, if a piece of shared information causes friction or misunderstanding, participants recognise that the information may cause a negative reputational evaluation. Four participants have deleted information in the past specifically because of the way it was perceived by their contacts:
- Jacqueline and Gillian deleted posts after someone reacted negatively, because they did not wish to be someone who would cause upset to someone else (Jacqueline; Gillian);
- James deleted a post then re-shared the information with altered language after a connection informed him that the terminology used in the initial post was not appropriate, and he did not wish to be thought of as someone who would use potentially offensive language (James);
- Helen deleted a post that she shared about a work colleague after being asked to do so: she recognised that it was necessary for maintaining a positive reputation at work, even though she was not personally concerned with how she would be perceived (Helen);
- Yvonne has not deleted information that has been misunderstood, but instead she engages with connections to re-state her position, feeling that it is an issue of adequate communication (Yvonne) or deletes the comments made by the other person (Yvonne).
Importantly, part of the process of managing personal reputations is by controlling or limiting with whom online information is shared. This shows that a key element in the management of personal reputation for all fifteen participants is determining with whom they will connect – as well as with whom they will not connect. This is especially relevant on Facebook, where there is an expectation of the platform as a private environment used to connect with family and friends. Amongst this group only James connects with clients and other industry contacts as standard practice (James). The remaining fourteen participants will only connect with professional contacts if there is also a personal or friendly relationship.
At the same time, participants tend to be more hesitant in unfriending individuals on Facebook, even after they have determined that they do not wish to be connected with an individual any longer. Instead, participants will manage their privacy settings to prevent individuals from viewing posts – sometimes in an effort to eliminate potential comments from the connection. Only Yvonne will unfriend or otherwise disconnect from anyone whom she feels is no longer relevant to her online social network – even if she wishes to remain in contact with them in an offline environment.
RQ3: How do individuals evaluate the identities and reputations of others based on the information available to them online?
With three exceptions (Kelly, James, and Yvonne), at interview the participants found it difficult to convey their evaluations of others based on the online information made available. However, it was clear that they are likely to view negatively anyone whose views are in stark contrast to their own. At times, this shared information can alter positive reputational evaluations, even if displayed just once (James). To a lesser extent, information that contrasts weakly with personal views and opinions can be viewed as a negative reputational marker if shared on a more frequent basis. This high frequency sharing of information can be evaluated more negatively than the same information would be if it were shared less often, or shared in conjunction with information that the evaluator views favourably.
The study participants exhibited conflicting views on the use of anonymous accounts and pseudonyms used by others. None of the participants viewed these types of accounts as completely acceptable, noting a level of scepticism, even if they understood why some individuals might use anonymous accounts and pseudonyms. For example, Jacqueline acknowledges that she is unlikely to give someone’s views credence if they are shared anonymously because she might question the individual’s motives (Jacqueline). However, she recognises that there are legitimate reasons why someone might want to hide their real identity, such as an activist or a member of the lesbian, gay bisexual, transgender community (Jacqueline). Gillian also expresses a level of conflict, questioning the accountability of information shared anonymously (Gillian). However, at the same time she accepts that some individuals might maintain anonymity because they are in situations where there might be risks if they were to identify themselves (Gillian).
All fifteen participants are more likely to be more forgiving or lenient in their evaluations of individuals that they know in an offline environment, especially if the information shared seems to be contradictory to the reputation they have built in the offline relationship. This forgiveness or leniency extends to individuals who share information that is in stark contrast to the participants’ own personal views and belief systems. Exceptions are also given based on the type of offline relationship that exists. For example, Yvonne makes exceptions for old friends and younger family members (Yvonne) when they post information that she does not like.
Thirteen of the participants did not feel that a lack of an online presence was a suitable indicator for making a reputational evaluation. However, two participants felt that a lack of an online presence or the inappropriate use of platforms would elicit negative reputational evaluations. One participant (Yvonne) feels that professional contacts (or potential professional contacts) who do not have an adequate online presence are incompetent or show a ‘lack of interest’. These evaluations make her reluctant to work with the individuals in question, in part because of the role they may later play in the maintenance of her own reputation (Yvonne). Similarly, Gillian drew attention to individuals who talk about the importance of digital yet they are ‘nowhere to be found [online]’, labelling them as ‘jerks’ (Gillian).
RQ4: To what extent are individuals actively practising identity and reputation building and evaluation online?
The levels of intentional reputation management by participants based on the platform they are using, and whether they are thinking about their professional or private reputations, varies across the group. At one extreme Helen (who only uses Facebook) shares what she wants without giving it much thought. This is on the basis that she is ‘inoffensive’ (Helen) and that others will not be judging her (Helen). At the other extreme Yvonne pays close attention to her information behaviour when interacting with social media. She said ‘[LinkedIn is] definitely my marketing tool. It’s very much about managing my reputation. It’s very much about building a reputation as well.’ (Yvonne), and that Facebook is ‘my site, these are my people, and I have control over what I post’ (Yvonne). She also actively curates her Facebook friends list to ensure that only a select group of individuals can see what she shares there.
The remaining thirteen participants display varying levels of intentional reputation management through the self-censorship behaviour noted above – even though their first concern is how information will be received by their contacts. Thus, there is lack of specific awareness regarding the management of personal reputation. Instead participants tend to do things (or do not do things) because they instinctively feel they should/should not. It was not until discussing their diary entries at interview did they consider the question of personal reputation management and evaluation on the basis of the sharing of online information – both by themselves or others.
Conclusions and next steps
There are some clear alignments between this work and reports of prior research. For example, this analysis supports findings from the literature review that relate to the self-regulation of online information sharing, and specific practices for individual platforms (Hagger-Johnson, Egan, and Stillwell, 2011; Ollier-Malaterre et al., 2013; van Dijik, 2013). It has also been confirmed that individuals manage the blurring of their private and professional personas by platform selection, or by controlling access to their posts by others, as has been previously identified by van Dijck (2013). Although they are doing it unconsciously, the individuals who have participated in this study to date are actively managing their reputations to an extent.
In some respects the analysis of this data set shows only partial matches with prior work, mainly related to practices for obscuring information. In short, the evidence presented here is weaker than that found in conclusions that derive from earlier studies such as the work of Bullingham and Vasconcelos (2013) on the use of pseudonyms as a way of experimenting with personalities or identities online, and other reports of the deliberate hiding of personal information in online profiles (Harviainen, 2014; Lingel and Boyd, 2013). The difference here is that the while participants in this study do engage in practices to mask their identities, this is not common practice, and nor is it for the purposes of creating separate or new online identities. The study’s findings on assessments of the quality and accuracy of information also show only a partial match with prior work. In this case it is the patterns of sharing that influence individuals’ assessment of the value here, rather than the information per se that has previously noted by other researchers (Ausloos, 2012; Carmagnola, Osborne, and Torre, 2013; Fertik and Thompson, 2010; Finocchiaro and Ricci, 2013; Labrecque et al., 2011; Lund, 2012).
There is also an instance where the findings of this study are at odds with reports of earlier research. Second-level connections have been noted in the past as important to reputational evaluations in the studies by Amichai-Hamburger and Vinitzky (2010), and by Boyd and Heer (2006). However, the participants here rarely pay attention to their connections’ connections. Even when they observe the value of a third party connection, this does not influence their assessment of the reputation of their own immediate connection.
Some new themes have emerged from this work to date, particularly with reference to the extent to which individuals actively practise identity and reputation building and evaluation online (RQ4). While this theme has been covered in the literature on citation practices in terms of the building, management and assessment of academic reputations (see Table 1), it has not been explored in the information science literature beyond this professional context or as related to ‘whole person’ reputations. To date this study indicates that overall levels of active identity and reputation building and evaluation using social media information vary and – on the whole – are low. Perhaps of most importance is that it is rare for individuals to consider the impact of information sharing on personal reputation building and evaluation. Indeed, these study participants revealed that they are more interested in the information that is shared than they are in the signals that this information might convey about the sharer(s).
It is evident from the above analysis that the larger doctoral study of which the findings presented here form a part has a contribution to make to theory development in information science, particularly with reference to human information seeking behaviour and use, following the tradition of previous studies of everyday life information seeking. It also has value in drawing on the literature on citation practices in extending knowledge on reputation management and evaluation based on shared information beyond the narrow context of academia.
A more detailed, analysis of the Generation X dataset – in combination with those for Generation Y and the Baby Boomers – will provide further insight on the specific theme of the role on online information on personal reputation management. This is due to be completed by autumn 2016. The findings of the full study of which this work is a part will be shared in 2017.
Acknowledgements
The authors would like to thank the study participants for devoting their time to this project, without which a study of this nature would not be possible.
About the authors
Frances Ryan is a doctoral student within the School of Computing at Edinburgh Napier University. She holds a Master of Letters in Media and Culture from the University of Stirling and a BA in Public Relations from Central
Washington University. She is currently exploring the role of online information in reputation management. Frances can be contacted at f.ryan@napier.ac.uk.
Peter Cruickshank is a Lecturer in Information Systems, School of Computing at Edinburgh Napier University. He holds an MSc in Computing from Edinburgh Napier University, and an MA (Hons) in Linguistics with Artificial Intelligence from the University of Edinburgh. His research interests include information governance and security, use of the internet by citizens and their representatives, and organisational acceptance of technology implementations. Peter can be contacted at p.cruickshank@napier.ac.uk.
Hazel Hall is Professor and Director of the Centre for Social Informatics within the School of Computing at Edinburgh Napier University. She holds a PhD in Computing from Napier University, an MA in Library and Information Studies from the University of Central England, and a BA (Spec Hons) in French from the University of Birmingham. Her research interests include information sharing in online environments, knowledge management, social computing/media, online communities and collaboration, library and information science research, and research impact. Hazel can be contacted at h.hall@napier.ac.uk.
Alistair Lawson is an Associate Professor in School of Computing at Edinburgh Napier University. He holds an MSc in Biomedical Engineering Science from the University of Dundee and BSc (Hons) in Applied Physics with Solid State Electronics from Heriot Watt University Edinburgh. His research interests include trust-based information sharing, and systems development for a range of applications such as health and social care, police and community partnerships, speech and language, and e-learning. Alistair can be contacted at a.lawson@napier.ac.uk.