Territorial barriers in interagency government data sharing
Jiangfeng Hu, Lihong Zhou and Di Wang
Introduction. Interagency government data sharing (IDS) is an indispensable precondition for the development of citizen-centred smart government. Adopting a theory of territoriality, this paper reports on an on-going research investigation, which explores, identifies, and qualifies the barriers to the lack of IDS.
Method. The research adopts an inductive approach, which combines a critical literature review, and three case studies in Central China.
Analysis. 118 articles, and 45 government officials and data managers from three regional government agencies collected as interview data were included and analysed using a thematic approach.
Results. nterorganisational dynamism affects the formulation of individual agencies’ psychological ownership on data, which leads to territorial marking and defending behaviours against IDS.
Conclusions. Territoriality theory offers a novel and useful perspective to interpret, understand and resolve IDS problems. Albeit this research is situated in China, the research findings offer valuable indications and insights that can be shared across international borders.
DOI: https://doi.org/10.47989/irisic2245
Introduction
Interagency government data sharing (IDS) is essential to the collaboration, coordination, and achievement of collective success across various government agencies (Zhou, et al., 2021). IDS can profoundly transform the present models of government operation by increasing openness and transparency, encouraging citizens’ participation and involvement, as well as by facilitating a paradigm shift from organization-centred to citizen-centred (Lips, et al., 2010; Scholl, 2012; Zhou, et al., 2020). Nevertheless, IDS is extremely difficult and challenging. It is a heavily concerned problem for governments and researchers around the world (Bajaj and Ram, 2007; Yang, et al., 2014; Wang, 2018; Zhou, et al., 2020).
Territoriality has been gaining attentions and studied by researchers from various academic fields in organisational sciences. It is the behavioural expression of an individual’s sense of ownership towards a physical, or social object (Brown, et al., 2005). In recent years, territoriality is viewed as a valuable theoretical perspective in information studies for interpreting and theorising the interplay of stakeholders in the creation, control, sharing and utilization of data, information, and knowledge (Larsen-Ledet and Korsgaard, 2019; Zhou et al., 2207).
Although IDS has been studied previously, it has rarely been investigated from the perspective of territoriality. Nevertheless, several prior studies generate implications, which suggest that territorial behaviours can severely hinder IDS (e.g., Das and Chakraborty, 2018; Zhou, et al., 2020). Territoriality can be a novel perspective for studying IDS. This research study aims to explore and identify causes of the lack of IDS by adopting the theory of territoriality as theoretical lens. Therefore, the following research questions were devised:
- How territoriality affects IDS?
- hat are the territorial barriers to IDS?
Research methods and processes
The research began with a general literature review. Two international (Web of Science, Scopus) and two Chinese (Wanfang, China National Knowledge Infrastructure) academic indexing databases were retrieved for relevant articles. After careful manual screening, a total of 118 articles were considered as relevant and included in the literature analysis.
To facilitate the analysis of literature selected, the research demised a preliminary analytical model based on Brown, et al. (2014), which propose that IDS problems can be resulted by three constructs: psychological ownership, inter-organisational dynamism, and territorial behaviour. The preliminary analytical model provided a lens for examining and coding the text of the articles, as well as a basis for comparing, differentiating, organising, and validating individual codes emerged.
It is important to note that the literature review provided a theoretical base, which is critical for the case study as the next stage of research. Specifically, the themes, sub-themes and codes adopted in the case study were used not only for the design of interview question script, but also a departing point for the analysis of interview data. This case study adopts a multi-case design, for which 45 leaders, public servants, IT professionals and data workers from three city governments in Central China were approached and interviewed. All interview recordings were manually transcribed and then uploaded to NVivo 11. The analysis of interview data was treated as a continuation of the literature analysis and inherited the thematic analysis strategy used in the literature review. The findings of the case study analysis are shown in Table 1 below.
| Theme | Sub-theme | Territorial xarriers (Codes) |
|---|---|---|
| Psychological ownership | Sense of data owning | |
| Institutional power assurance | ||
| Institutional status assurance | ||
| Territorial behaviour | Identity-oriented marking | Identity-oriented data system infrastructure |
| Identity-oriented data annotation | ||
| Control-oriented marking | Complicated management procedures marking | |
| Limited data provision marking | ||
| Anticipatory defence | Anticipatory usage of special line and intranet | |
| Anticipatory shield of independent network cards | ||
| Anticipatory password setting | ||
| Anticipatory usage of digital certificates | ||
| Reactionary defence | Directly or indirectly refusing defences | |
| Official reactionary proceedings | ||
| Interorganisational dynamism | Political structure | TIAO KUAI government structure |
| Lack of IDS law and policy | ||
| Interorganisational relationship | Lack of previous collaboration | |
| Lack of interorganisational incentive | ||
| Interorganisational risk management | Unclear interorganisational data responsibility | |
| Data reliability concern |
Research findings
Psychological ownership of data
Many interview respondents explicitly stated that they understand ‘data all belong to the government’ (Interview E1). Nevertheless, data from all three case studies showed that ‘all departments are not willing to share their data’ (Interview N2). Almost all government agencies firmly believe that ‘data is ours’ (Interview E1). Thus, if an agency need data from others, the behaviour can be interpreted as ‘not just taking advantage of our data, but also taking advantage of us’ (Interview V2).
‘They just hold their data as something in their own pocket. A lot of people believe in so because they have yet reached the level of awareness. Why they need to let others use their own data?’ (Interview A2)
Moreover, the data analysis showed that data must be carefully protected as they are a source of ‘institutional power’ (Interview E1). In this case, sharing data can be seen as sharing and releasing power to other agencies. Furthermore, Data stored and managed by individual agencies can also be critical asset for ‘protecting an agency’s status’ (Interview C2). The concern is that once the data are shared, their status, functions and services can potentially be replaced by other agencies. ‘This is a survival problem’ (Interview C2). Therefore, IDS is likely to be viewed as a potential threat, and thus should be carried out cautiously.
Territorial behaviour
The data analysis identified that government agencies use unique data infrastructure to process and store their self-generated data. In this case, they usually have different data formats and annotation, which are useful to reflect an individual agency’s identity and distinguish from that of others. Besides, since these ‘multifarious systems’ (Interview I1 and J1) are equipped with various standards and interfaces, the incompatible data systems have established strong and rigid defence walls against IDS.
‘Processing one thing needs to work through eight different data administration systems, with eight exclusive accounts and passwords. Besides, these systems use different VPNs and independent network boards so that government workers have to operate and switch from those systems several times in practice’ (Interview H1).
Furthermore, government agencies actively developed complicated management procedures to better control their owned data, which also aims to communicate the sharing boundary of the data and send a public message claiming that they have psychological ownership over it. To some extent, this can prevent potentially improper IDS requesting from the beginning. In principle, individual agencies should ‘apply to the superior agencies for IDS permission’ (Interview I1 and J1). After that, an ‘official statement’ (Interview B2&K2) for data application is essential. Even so, ‘data are not shared unconditionally’ (Interview K2), as one of the respondents stated, ‘they can see the data’ (Interview T2), but not ‘take them away’ (Interview B2).
‘The Bureau A has an internal information system, which offers no external accesses. When we need data from the bureau, they will print a form [the data] out for you. If we really need to use their system, we can send a formal application. Then they will operate their system, whereas we can only observe. We cannot get our hands on their system.’ (Interview U2).
Moreover, individual agencies generally choose to 'provide limited data' (Interview A1 and B1) that are all ‘fundamental ones’ (Interview P2 and V2). Therefore, it is scarcely possible to share amount of valuable data such like ‘ID and phone numbers’ (Interview V2), ‘census information’ (Interview P2), and ‘GPS’ (Interview G1) because they are quite ''confidential’ (Interview G1) and this behaviour is regarded as a ‘protection of citizen’s privacy’ (Interview V2).
However, the data ownership among individual agencies are ambiguous and the management procedures are quite diverse and complex. It is unavoidable that sometimes government agencies will make wrong operations unintentionally during the process of data application. To thwart such infringement actions from others effectively when they occur, government agencies commonly act defending behaviours, such as usage of ‘the special line and intranet’ (Interview G1 and H1) on data systems in advance, with ‘independent network cards to shield’ (Interview H1) incorrect data requesting from the extranet.
‘Other agencies are different from us, as we use the intranet. Moreover, telephone battery charging, and USB drive insertion are not allowed on our computers. Apart from that, computers used for two purposes are strictly forbidden. All computers are under real-time monitoring.’ (Interview J2).
Additionally, ‘password setting’ (Interview G1 and H1), and the use of ‘digital certificates’ (Interview J2) that distinguish the authority of data acquisition are also prevailing defences individual agencies taking before violations of unnormal data requesting.
Moreover, as shown from the data collected, in action to an attempt of data requesting, it is very common that an individual agency also perform defences of directly refusing IDS requests from others face to face, with ‘no formal procedures’ (Interview N2) as an excuse. In some cases, instead of head-on incoordination, they prefer more gentle ways to evade or stonewall data applications.
‘The Bureau B once consulted us for a case because they thought that we have the useful data. Honestly, they can obtain the data at an available website. Unfortunately, they did not realize. But still, we did not tell them the truth or offer them any data. Instead, we just suggest them to ask other agencies for help.’ (Interview R2).
Albeit it is scarcely that data misuse or abuse will happen among individual agencies, once IDS officially begins, there still are official proceedings for defending after their rights or interests get affected. In general, ‘a statement or a call initially, suspending IDS subsequently, and accountability ultimately’ (Interview E1 and G1).
Inter-organizational dynamism
As shown from the data collected, ‘Tiao-Kuai government structure is a unique existence’ (Interview A1 and B1) in socio-politically environment of China, which tremendously affects IDS. A Tiao stands for the vertical relationships between government agencies belonging to a same functional administrative system, whilst a Kuai refers to horizontal relationships between agencies of different administrative functions at the same government level.
The data analysis identified that Tiao is much more powerful than Kuai. Thus, IDS willingness in Tiao is quite stronger because government agencies regard it as ‘charging their own data’ (Interview E3). Conversely, ‘IDS is limited in Kuai’ (Interview G3) as individual agencies commonly have no desire to give their own data away.
‘Many individual agencies need our data, but marriage data belongs to individual privacy. Therefore, at the municipal level, we never solely give any agencies our marriage data, but submit all of the data to our superior agency.’ (Interview M2).
Also, current IDS laws and policies are not effective enough to truly propel the development and implement of IDS because they are ‘rather broad’ (Interview L3) without ‘specific implementation details’ (Interview L3 and J3). One of the respondents stated, ‘although IDS essentially relies on network platforms, it is much more efficient that the government publishes a document to demand IDS immediately as the visible hands are more powerful’ (Interview V2).
Therefore, there has been ‘few or even no IDS collaboration’ (Interview A3, C1 and D1) among different functional agencies at the same level. Although horizontal collaboration attempts happen sometimes, ‘IDS has never been truly successful’ (Interview C1 and D1). One of the respondents stated that ‘experiencing of being rejected discourage them from making IDS request’ (Interview G1).
‘Bureau C, Bureau D, and Bureau E had a cooperation before. During the cooperation, Bureau D can apply Bureau E for transportation data and the latter bureau will offer whatever they need. However, there is no direct collection or collaboration between the former one and Bureau C.’ (Interview G1).
Meanwhile, it worth noting that ‘the absence of performance evaluation systems’ (Interview C3 and G3) plays a vital role in the negativity of IDS among individual agencies, as a unified mechanism offering stress and inspiration can provide the IDS dynamism among individual agencies.
Yet, individual agencies are reluctant to IDS probably because of unclear data responsibility. According to all three cases, although Bureau E is taking charge of IDS, ‘the responsibility has not been explicitly defined yet’ (Interview S2). Moreover, it is commonly believed that data reliability may at risk sometimes. One of the main concerns that respondents mentioned most is ‘data are not the latest’ (Interview A2) because they are always ‘not uploaded timely when changes happen’ (Interview U2).
Discussion
The following diagram is developed to better conceptualise the research findings. As shown in Figure 1, because of Tiao Kuai government structure, absence of collaborative experiences, and unclear data responsibility, individual agencies are difficult to form positive dynamism, which makes it easy for them to emerge profound psychological ownership on data. Thereafter, becoming very cautions in acting territorial marking and defending behaviours at different stages to protect their territories and hinder IDS. It is necessary for the central government to identify individual agencies’ typical territorial behaviours and the causes.
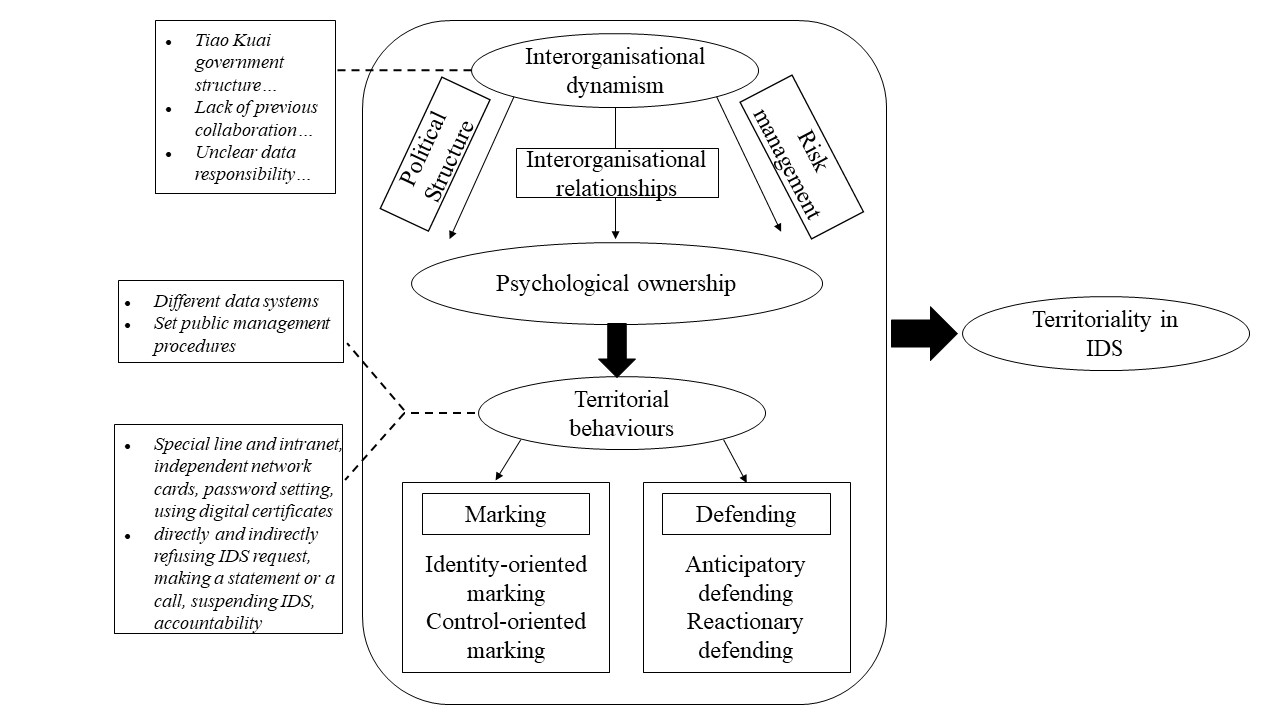
The conceptualisation indicates that psychological ownership is the main cause of territorial behaviours. Therefore, to improve IDS, efforts and strategies should be developed aiming at promoting the awareness of government employees, who should fully understand that government data do not belong to any organisations, but the entire government entity. Also, as informed by the conceptualisation, the government structure, technical infrastructure, and privacy rules can cause psychological ownership and enhance territorial behaviours. In this case, it is necessary to review and revise existing infrastructure and rules, which should be more compatible and supportive to IDS.
Moreover, it is worth noting that the Tiao Kuai government structure is so strongly rooted in Chinese traditional bureaucratic culture that hardly possible to change. However, great support from the centre government is vital for IDS. Hence, publishing concrete laws and policies, establishing effective supervision and incentive mechanism, explicating data responsibility, and providing sufficient technical and financial support are effective for propelling IDS. Conclusion
Conclusion
This paper reports on an on-going research investigation, which aims to study government employees’ territorial behaviours as barriers to IDS. The research design included a critical literature review and a case study. The literature review offered a theoretical perspective and informed the latest development in related fields, whereas the case study aimed to explore and understand territorial behaviours in the real-life context. It was identified and confirmed that four types of territorial behaviours can severely hinder IDS. These territorial behaviours are identity-oriented marking, control-oriented marking, anticipatory defending, and reactionary defending. Also, the research findings show that the territoriality theory offers a novel perspective to study IDS problems.
However, as an on-going project, the research team is currently collecting more interview data from the case studies to establish more specific and pragmatic strategies to mediate territorial behaviours and strengthen IDS.
About the authors
Jiangfeng Hu is a master student at the School of Information Management, Wuhan University, China. She obtained her bachelor’s degree from Wuhan University. Her research interests are in the area of interagency government data sharing. She can be contacted at: jiangfeng.hu@whu.edu.cn
Lihong Zhou is a professor and the Associate Dean at the School of Information Management, Wuhan University, China. He obtained his PhD in information studies from the University of Sheffield, UK. His main research areas are cross-boundary sharing of information resources, as well as digital scholarship services in academic libraries. He can be contacted at: l.zhou@whu.edu.cn
Di Wang is a postdoc researcher at the School of Information Management, Wuhan University, China. She obtained her PhD in computing from Macquarie University and another PhD in Information Resources Management from Wuhan University. Her research focuses on big data analytics and open data resources. She can be contacted at: di.wang@whu.edu.cn
References
- Bajaj, A., & Ram, S. (2007). A comprehensive framework towards information sharing between government agencies. International Journal of Electronic Government Research (IJEGR), 3(2), 29-44. https://doi.org/10.4018/jegr.2007040102
- Brown, G., Crossley, C., & Robinson, S. L. (2014). Psychological ownership, territorial behavior, and being perceived as a team contributor: The critical role of trust in the work environment. Personnel psychology, 67(2), 463-485. https://doi.org/10.1111/peps.12048
- Brown, G., Lawrence, T. B., & Robinson, S. L. (2005). Territoriality in organizations. Academy of Management Review, 30(3), 577-594. https://doi.org/10.5465/amr.2005.17293710
- Das, A. K., & Chakraborty, S. (2018). Knowledge withholding within an organization: the psychological resistance to knowledge sharing linking with territoriality. Journal on Innovation and Sustainability RISUS, 9(3), 94-108. https://doi.org/10.24212/2179-3565.2018v9i3p94-108
- Larsen-Ledet, I., & Korsgaard, H. (2019). Territorial functioning in collaborative writing. Computer Supported Cooperative Work (CSCW), 28(3), 391-433. https://doi.org/10.1007/s10606-019-09359-8
- Lips, M., Eppel, E., Cunningham, A., & Hopkins-Burns, V. (2010). Public attitudes to the sharing of personal information in the course of online public service provision. Victoria University of Wellington. http://e-government.vuw.ac.nz/summary_IRD.aspx (Internet Archive)
- Scholl, H. J. (2012). Five trends that matter: Challenges to 21st century electronic government. Information Polity, 17(3, 4), 317-327. https://doi.org/10.3233/IP-2012-0280
- Wang, F. (2018). Understanding the dynamic mechanism of interagency government data sharing. Government Information Quarterly, 35(4), 536-546. https://doi.org/10.1016/j.giq.2018.08.003
- Yang, T. M., Pardo, T., & Wu, Y. J. (2014). How is information shared across the boundaries of government agencies? An e-Government case study. Government Information Quarterly, 31(4), 637-652. https://doi.org/10.1016/j.giq.2014.05.002
- Zhou, L., Chen, L., & Han, Y. (2021). “Data stickiness” in interagency government data sharing: a case study. Journal of Documentation, 77(6), 1286-1303. https://doi.org/10.1108/JD-04-2021-0087
- Zhou, L., Huang, R., & Li, B. (2020). “What is mine is not thine”: Understanding barriers to China's interagency government data sharing from existing literature. Library & Information Science Research, 42(3), 101031. https://doi.org/10.1016/j.lisr.2020.101031